In his latest blog, Andrey Yakovlev, security researcher at IntSights, discusses the ‘gangsomware’ group, Darkside, their reasons behind the Colonial Pipeline ransomware attack and whether they even meant to cause so much unrest, as the group claims to be ‘apolitical’ and does not wish to be associated with the Russian government. Interesting.
The ransomware attack on the Colonial Pipeline has (and still has) the potential to devastate the US. Independent oil market analyst Gaurav Sharma told the BBC that a lot of fuel was now ‘stranded’ at refineries in Texas and, “Unless they sort it out by Tuesday, they’re in big trouble.” Well, Tuesday happens to be today so it’s going well so far.
“The first areas to be hit would be Atlanta and Tennessee, then the domino effect goes up to New York.” He said oil futures traders were now ‘scrambling’ to meet demand, at a time when US inventories are declining.
Of course, when news of a ransomware attack on a national asset such as an oil pipeline makes the rounds – as it has in this case – the first conclusion is usually that this was the result of a nation-state attack.
To be sure, countries such as Russia and China are continuously seeking ways to disrupt their geopolitical adversaries; however, the Colonial Pipeline case involving the DarkSide group is both unique and the sign of an important trend in what Andrey Yakovlev refers to as to as ‘gangsomware’.
The story of DarkSide
It’s been widely reported that Colonial Pipeline was compromised by a Russian group named DarkSide. Their affiliate programs have been present in the cybercriminal underground since at least November 2020:
In February 2021 they went for a little hiatus to update their product and after a month they rolled out the new version in a separate forum thread:
Without directly claiming responsibility, DarkSide has responded to the news stories naming them by saying they are ‘apolitical’ and are just in business to ‘make money.’
Here is the DarkSide-issued statement:
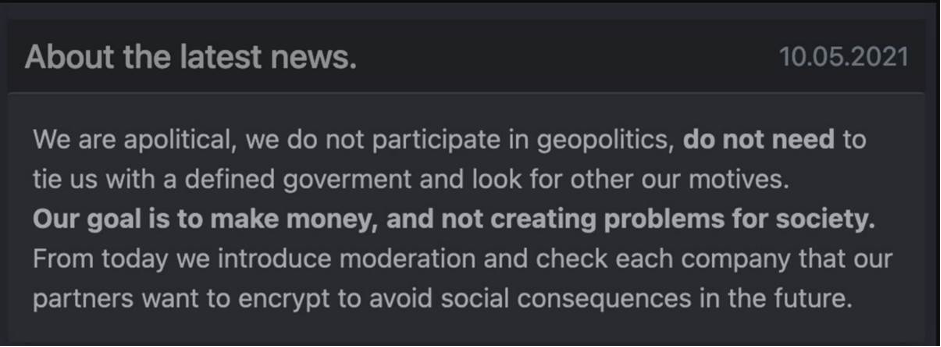
What’s interesting in the above statement is that the group does not want to be associated with the Russian (or any) government, nor does it want to be seen as a ‘bad guy.’
Andrey is of the opinion that they got a little bit overwhelmed by the media coverage and all the attention it brings to Russian cyber-offensive.
There didn’t appear to be any direct statements that ‘DarkSide equals Kremlin,’ but there has recently been a lot of news related to Russian state-sponsored attacks (SolarWinds, for example) so the DarkSide statement was perhaps a preventive measure, to differentiate from the Russian government in the beginning.
Gangsomware and DarkSide
DarkSide wants to be utilised as a service organisation – ransomware-as-a-service, to be exact. In fact, they have taken the ‘service’ part of their affiliate program to a new level of standard. They have service phone numbers, a ticketing system, and they actively ask press and recovery companies to engage with them. It also seems like they polished surrounding aspects of their production chain.
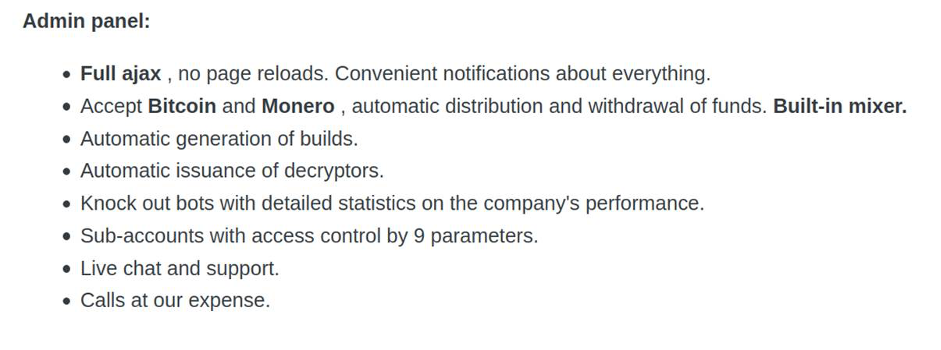
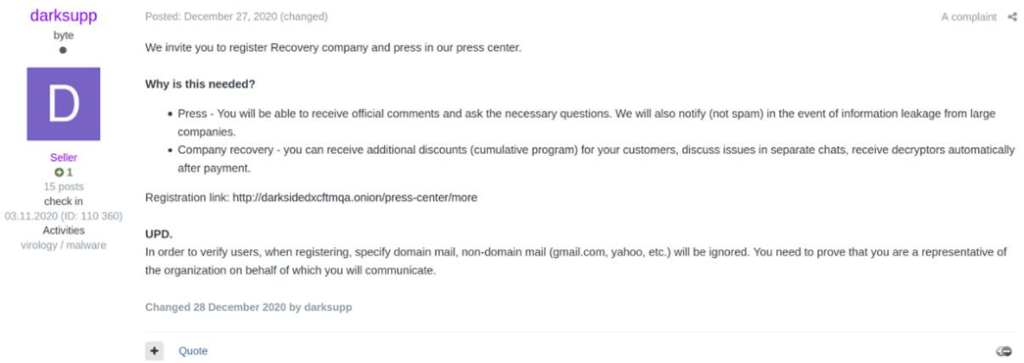
For example, a technically exceptional ransomware strain would miss out on potential payments if they lack the support systems mentioned above.
DarkSide boasts to be one of the fastest in terms of encrypting the victim’s files (they tested their ransomware against a competing program and also received praises from threat actors that tested).
So, in short, not only is DarkSide’s malware sophisticated and constantly updated, but the organisation itself also fine-tunes the extortion part with comfortable and easy-to-use interfaces and solutions.
The end game
While DarkSide and other gangsomware groups may not intend to cause harm to society in their endeavors, the impacts of their actions are increasingly devastating at a local, national, and even global level.
The Colonial Pipeline attack has severely crippled the US fuel supply chain by taking Colonial’s main pipelines offline for what will be days, and perhaps could become weeks.
The service organisation model employed by groups such as DarkSide is an important trend in ransomware activities that are meant to maintain at least some level of decency making as much money as possible.
For example, they do not target certain industries and services such as healthcare (how very decent of them). Although while not specifically targeted toward bringing down critical infrastructure, these attacks are a wake-up call for organisations with related supply chains.
DCR Live | The virtual event coming to you June 29 & July 1 | Find out more and register here.

